Security Event Triage: Operationalizing Security Analysis
Security Event Triage: Operationalizing Security Analysis
Collect all the data!
Photo: Aaron Rosenmund aka. IRONCAT
Keeping up with advanced cyber threats and sifting through the insurmountable number of alerts available to security analysts is not sustainable without leveling up your security analysis skills to keep pace with modern security operations. In this course, Security Event Triage: Operationalizing Security Analysis, you will gain foundational knowledge of modern cybersecurity continuous monitoring techniques and processes. First, you will learn how the security analyst fits into the overall cybersecurity posture of an organization. Next, you will discover the technologies and methodologies covered in the security event triage path. Finally, you will map the knowledge, skills, and abilities taught in each of the security event triage courses to the MITRE ATT&CK techniques that comprise the chain of compromise used by the simulated threat actors. When you’re finished with this course, you will have the skills and knowledge of security analysis needed to identify and interrogate all manner of cyber threats.
Coverage and Purpose
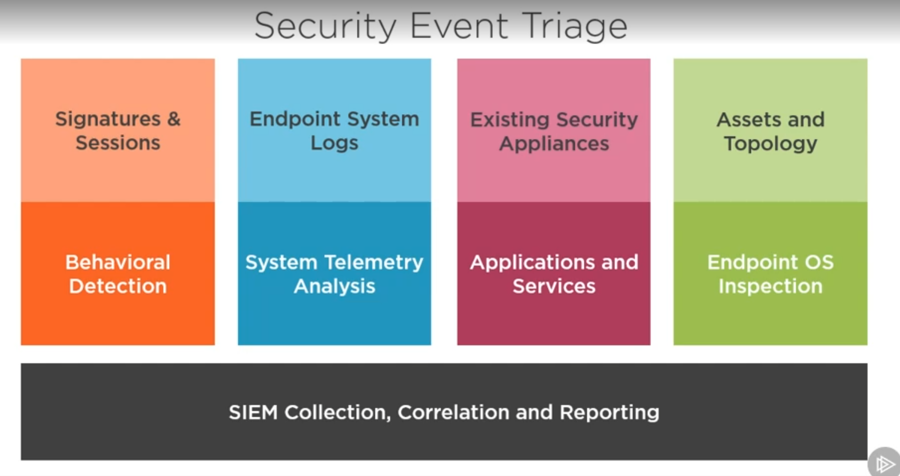
Security operations means a lot of things to a lot of poeple, but at the end of they day, your job as a security analyst is to detect threats. To detect threats, you have to actually find them. To find them, you need to look. And to look, you need to have access to the data that has the clues and evidence of attacks. Different attacks require different kinds of data, sometimes multiples views of data to find anomalies and indicators of compromise. Doing all this in an enterprise environment is kinda a lot, and this course covers a general framework for how that is done and the data required, setting you up for deeper dives into specific detections in individual data sets.
Becoming the Calvary
To put things in context, get familiar with the scenario, risk and the kinds of tools and techniques that are used to defender agains modern cyber threats. You have to meet the enemery where they are, and to do that, you become the calvary.
Modernizing Security Operations
What it comes down to is that there are simple detections looking for signatures in network and log files. And then there are more complicated detections that look for various types of anomalies with machine learning methods. Ultimately, if you are doing it right, you are still going to have a ton of false positives and frankly data that just doesn’t mean all that much on it’s own. But after you add in some threat intelligence to put context to the data, and look at correlations between time and locality of the alerts. You can widdle down the noise to some very high fidelity alerts to investigate with your resource constrained teams. It is all about organizing the technology and the people into the right workflow.
Learning Security Event Triage
The skills that follow this ourse are specific, and focused. They cover the CSWF role of a cyber defense analyst, but not everyone needs every single skill set. (I don’t know why you wouldn’t want it, but still.) Getting the information needed to focus on the TTPs that matter is what this is about. Getting you, the learner to the information you need as fast as possible.
Sounds Great, How do I Get This Course?
This course is hosted on www.Pluralsight.com and is part of the Security Event Triage Skill Path, and does require a subscription. However, pluralsight often hosts free weekends and sometimes free months! For instance April was free in 2020, and 2021. So be on the lookout.