Security Event Triage: Revealing Attacker Methodology in Web Application Events
Security Event Triage: Revealing Attacker Methodology in Web Application Events
You can't detect what you can't see.
Photo: Aaron Rosenmund aka. IRONCAT
Developing the skills necessary for a security analyst to accurately detect and triage adversary tactics and techniques applied to web applications requires experience with web application’s baseline behavior and the use of advanced detection capabilities. Neither of which are easy to obtain. In this course, Security Event Triage: Revealing Attacker Methodology in Web Application Events, you will gain the foundation knowledge and experience with web application technologies and attacker methodologies required to protect your vital business functions. First, you will monitor the front door of applications for common attacks with web application firewalls on-premises and on major cloud platforms. Next, you will learn the logic behind hunting for behavioral anomalies generated by more advanced attacker activity and how to create machine learning jobs to identify this behavior in an automated way. Finally, you will discover how to leverage the same tools the attackers use to actively spot holes in your applications that pop up as new builds are released and mitigate the associated risk. When you finish this course, you will have the skills and knowledge of web application attack detection needed to implement continuous monitoring capabilities that protect the enterprise applications on which your organization depends.
Coverage and Purpose
Defending Against Web Application Attack Techniques
If you aren’t familiar with web application attacks, it will be really hard to defend agains them. Yes, web applications vary and there are many different tech stacks to worry about. But in this module, attacks from a technology agonostic perspective are covered, as well as how to catch their behavior regardless of the specific tech stack. I introduce Mitre Att&ck components related to web application exploitation and cover the basic resources such as OWASP and where to find them.
Detecting Attackers with Web Application Firewalls
I know there are all kinds of firewalls to worry about. Many firewalls say that they can also cover application layer. Call themselves next-gen and all that. I am here to tell you that your web applications need to have a dedicated web application firewall. More than that, it needs to be integrated into your continous security monitoring cycle. Just like suricate, snort or a antivirus, you can update you web application firewall with community, vendor or custom rules. In this module I cover the use of ModSecurity, AWS WAF and Azure WAF. In each, you will learn how to set them up, how to update rulesets, and how to read the output and intgerate the output into your detection workflow. Culminating in the triage cross stie scripting, LFI and SQLi.
Log Collection and Analyzing Application Behavior with Logs
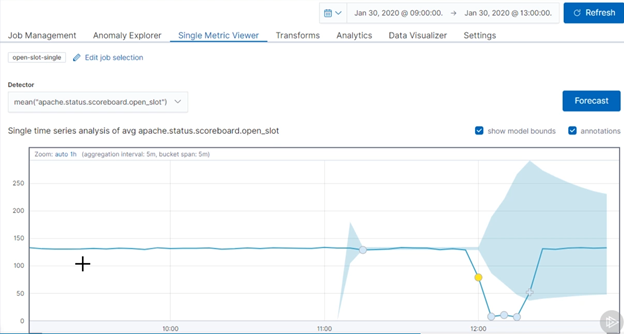
Web applications, whether, nginx, apache or any other technology, will always have logs. Traditionally, these logs are leveraged to troubleshoot, or monitor web access from a IT-OPS or DEV-OPS perspective. Just like with any other area of technology, these are also great signals for security detections! In this module, I cover novel, behavioral methods for detecting enumeration, DOS, and Timing Based SQLi. The access logs are generally ubiquitous acorss server technologies. Enumeration is generally detected by string signature alerting on specific files attempting to be accessed. There are better ways! Get less false positives by leveraging statistical regression analysis across http codes by requesting IP! Worried about DOS attacks on apache? Here I teach a new way to monitor worker status to quickly identify a slowloris type attack. SQLi timing based attacks are notoriously difficult to detect, that’s okay…response times from posts should be relativley consistent across a given page. You can identify the latency and realize you either have an actually IT-OPS issue or a potential security event with the concepts revealed covered in this module.
Integrating Web Vulnerability Scanning Detections
Not unlike using NMAP to map your network continuous to identify changes in exposed ports and devices. You can do the same with vulnerability scanners. Pipe the resulting information into a siem or database, and monitor the changes over time. When you see an event or get a suspicous spike in odd behavior from another detection, if it correlates with a page or component in this vulnerability set of data, you now have much more context and confidence around the severity.
Operationalizing Web Application Attack Detection
Your threat surface and risk define your need for mitigation through detection. In the case of web applications, you need to be sure that you have detection coverage for each type of attack. Prefferably you leverage behavioral methods to reduce the overhead of static signatures. Combining both is the way to go, and allows you to manage the processing load, and WAF requirements as you learn to phase out large swaths of signature detections with behavioral methods. Remmber…always test, that is why emulation is such a key component of your cyber security operation function.
Sounds Great, How do I Get This Course?
This course is hosted on www.Pluralsight.com and is part of the Security Event Triage Skill Path, and does require a subscription. However, pluralsight often hosts free weekends and sometimes free months! For instance April was free in 2020, and 2021. So be on the lookout.